In the era of the internet, email marketing has become an integral part of any business’s growth. More than 4 billion people use email globally, making it by far the most expansive marketing channel.
Due to COVID-19’s continued relevance in our daily lives, consumers are using email more than ever. This explains why over 60% of consumers still prefer email communication to engage with their favorite brands.
You can only get conversions from this type of email if it reaches your target consumers, otherwise, the return on investment is significantly reduced. To ensure email deliverability, you need a foolproof authentication process. Find out what email authentication is and how your company can benefit from by authenticating emails.
Before we get started, let me remind you about the importance of email deliverability.
Email Authentication: What is it?
An email becomes authenticated when it passes a verification process that verifies your domain and email address before it can be sent through an ESP. It has to pass this verification process to be authenticated.
A lot of spam was sent by businesses in the past when they could buy email lists and spam random people. In response to spam content in emails, anti-spam agencies and top companies – including Yahoo and the Anti-Spam Research Group (ASRG) – pooled resources to create an email authentication protocol.
Due to this, they developed several authentication methods to prevent harmful content from entering the network.
Methods of Authenticating emails
Simple Mail Transfer Protocol (SMTP) servers only receive and send emails without requiring any authentication. To ensure the security of mail transfers, these servers require additional authentication standards.
To combat spam in the early days of the internet, the Internet Engineering Task Force (IETF) introduced email protocols.
The following email authentication methods have been developed by their research and persistent efforts:
Sender Policy Framework (SPF)
An SPF record informs a receiving server about an authenticated IP address and domain. SPF records are DNS TXT records associated with a specific domain (or range of addresses belonging to the same network) received by the server.
The first widely recognized email authentication protocol, SPF, was created in the early 2000s.
To determine an email’s authenticity, senders without valid SPF records often undergo stringent secondary verification. Typically, these emails end up in spam folders.
SPF authentication is sometimes enough to protect against spoofing and other malicious emails, but it does not offer full protection. In addition, after changing ISPs, you need to update your records.
DomainKeys Identified Mail (DKIM)
OpenDKIM (DomainKeys Identified Mail) is used to generate the encrypted tokens required to validate the sending address on the recipient’s server when using DKIM (DomainKeys Identified Mail).
To determine whether the original content has not been altered during transmission, DKIM uses two encryption keys – a public one and a private one.
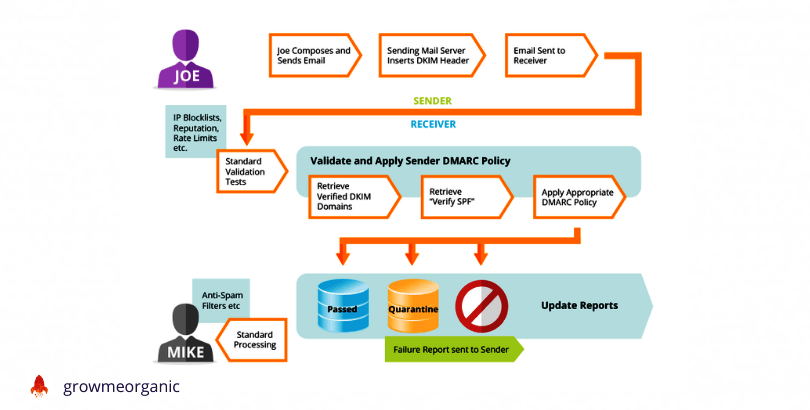
Domain-based Message Authentication, Reporting & Conformance (DMARC)
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a method for verifying the message source and generating reports about how the message complies with specified rules.
When requests are sent to the receiving server, DMARC works in conjunction with SPF or DKIM. If the source domain has not been authenticated, these requests inform the server what to do. These are the DNS records for DMARC actions:
The receiving server does nothing when p=none is set.
p=reject – any mail that fails authentication (SFTP or DKIM) is rejected by the receiving server.
P=quarantine – if the email is unconfirmed, the mailbox flags the message as suspicious and puts it in the spam folder.
V -dmarc is checked by the receiving server.
Additionally, DMARC can be configured to send authentication status information to your preferred email address. You can monitor your domain and prevent spoofing by using the data from these constant updates.
Authentication of Emails: What Does It Entail?
Every authentication technique has its working principle, but in general, authentication follows a standard procedure.
- Verifying the domain and the sending address is part of the authentication protocol.
- In the DNS records, the domain owner adds the encryption keys and records.
- Incoming messages are authenticated by the receiving server using the private key.
- Depending on the receiving server, the message is sent, rejected, or quarantined.
Authentication is the First Step
The authentication process sounds complicated based on the issues discussed above. What’s the point of authenticating emails and your domain if your business doesn’t use them?
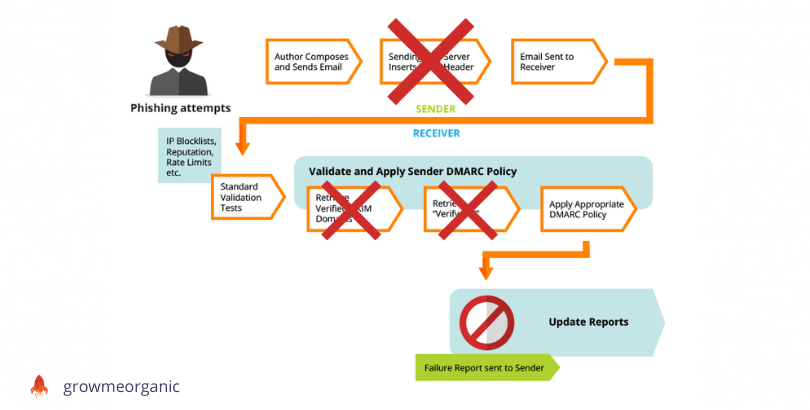
Phishing Prevention
Before reaching the recipient, your company’s emails are sent through SMTP servers. Malicious actors can attack these servers. If you want to review and test your email campaigns before they are sent, you can set up a fake SMTP server.
Phishers can bypass standard checks by simulating your domain or email address using advanced mail servers. Due to the DMARC protocol, they are unable to access the recipient server, which means that the message can’t be delivered.
When you receive the report, you can use it to blocklist these emails and protect your IP address.
Deters scammers
Using your company’s name, scammers can defraud your customers or spread false information about your business.
Nearly 800,000 online fraud cases have been reported to the FBI’s Internet Crime Complaint Center (IC3), causing financial losses of over $4.2 billion. Those are only the cases reported to the FBI!
However, how can you prevent consumers from falling victim to these scams?
Users can only receive authenticated emails from email service providers. In addition, you should give your mail provider access to your PTR record to verify your brand’s identity (as is the case for GrowMeOrganic users with dedicated IPs).
Enhances your brand’s reputation
Through email authentication, brand domain names and email addresses are verified, thereby establishing legitimacy for your brand. A DMARC authentication protocol ensures your consumers won’t receive phishing emails from ‘you’. The result is that your brand will appear trustworthy.
You must authenticate your email to validate your online presence since every company relies on reputation to boost sales.
Increasing email deliverability
Now that you understand why your brand’s email deliverability needs improvement, let’s explore ways to improve it.
Mobile optimization
Brafton states that 75% of consumers will not read your email if it’s not mobile-friendly. Smartphones are also used by over 40% of internet users.
Thus, optimizing your emails for mobile makes the content easier to deliver and more likely to attract customers’ interest.
Maintain a clean email list
Subscribers to your newsletter give consent for you to send them emails. Inactive emails can hurt your email deliverability, even though these permissions are valid. To detect spam, ESPs use spam traps. Decluttering your email list can help you avoid falling into these traps.
Refine the content
The use of images by spammers has always been a way of evading text-based authentication protocols and spam filters. As an unfortunate coincidence, consumers digest text better than visual information.
There is a dilemma here: should text in an email be accompanied by images?
Use images ONLY to supplement your email text if you want to reach more people. By doing so, your email will be accepted by spam filters as well as consumers.
Don’t shorten URLs
In email marketing, URL shorteners are a major red flag: they indicate that you are trying to conceal something. Additionally, scammers often use shortened URLs to disguise their true domain.
When you link to your email content, use hyperlinks. If necessary, leave the original URL.
About Post Author
Anant Gupta
Growth Hacker, Marketing Automation Enthusiast & Founder of GrowMeOrganic